Bounty in the Code: Hunting Secrets in JavaScript
— Sam Jacob Dec, 2, 2023
JavaScript stands as a cornerstone of modern programming languages, known for its versatility, flexibility, and ease of use.
Its agility allows developers to craft dynamic and interactive web experiences, making it the go-to language for client-side scripting. With JavaScript, the possibilities seem boundless, as it empowers developers to create responsive websites and applications with fluid functionalities.
It seamlessly adapts across multiple platforms and environments, fostering the creation of cross-platform applications. This adaptability extends to a vast ecosystem of frameworks and libraries such as React, Angular, and Vue.js.
Key Dimensions and Dynamic Capabilities of JavaScript:
- Interactive: JavaScript is like the magic wand that makes web pages fun to use. It lets developers create things like cool image slideshows, pop-up boxes, and tooltips. You can click on stuff, and it responds without reloading the whole page.
- Dynamic Content: Think of JavaScript as the secret sauce for real-time updates. It helps web pages show you the latest information without making you wait for the whole page to load again. This is handy for things like live social media feeds or chat, making the page feel quick and responsive.
- Form Validation: Ever filled out a web form and gotten frustrated when you hit “submit” and it yells at you for missing something? JavaScript helps check your inputs as you type, so you get a heads-up if you make a mistake. That way, you’re less likely to submit incorrect info or forget something important.
In this blog, we aim to provide a comprehensive understanding of JavaScript, navigating through its strengths and weaknesses. We will talk about penetration testing (bug-hunting) techniques in JavaScript and how to uncover secrets and sensitive data in JS files manually and in an automated fashion.
Importance of reconnaissance through JavaScript:
In the realm of penetration testing, we all know that reconnaissance process is pivotal for identifying vulnerabilities and potential points of entry into a system. When it comes to web applications, checking JavaScript is of utmost importance during this reconnaissance phase. JavaScript, being a dynamic and widely used scripting language on the client-side, plays a critical role in the functionality and interactivity of modern web applications. Analyzing JavaScript code and understanding the intricacies of JavaScript aids penetration testers to:
· Identify new Endpoints and parameters.
· Explore hidden feature which application may not be using
· Hidden or internal portal/subdomains
· Identifying client-side weaknesses that might not be apparent through traditional testing methods.
By scrutinizing JavaScript during reconnaissance, as penetration testers we can gain insights into the application’s attack surface, enabling us to formulate more targeted and effective strategies to uncover and address security vulnerabilities, ultimately enhancing the overall resilience of the web application against potential cyber threats.
While there are several security vulnerabilities on the client-side scripts, in this blog we will deep-dive specifically on discovering sensitive Information and insecure data handling (API key, authorization or tokens, leaked credentials, AWS and oath secrets etc.) from Javascripts.
Importance of reconnaissance through JavaScript:
- Inspecting JavaScript code: One of the simplest and straightforward approach is to manually explore the JavaScript file on client-side. In your web browser, right-click on the web page and select “View Page Source” or “Inspect.” This will open the developer tools, and you can navigate through the HTML source code. Look for JavaScript references within the HTML file, which are often included using <script> tags. You can click on these references to view the JavaScript code. In several occasions, developers inadvertently include sensitive data such as passwords or API keys directly within client-side JavaScript code. Detecting this information within the JavaScript code does not necessarily demand an extensive background in JavaScript programming, nor does it necessitate many years of experience.
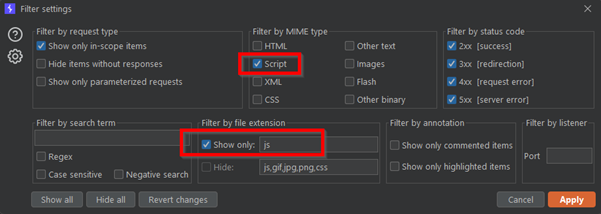
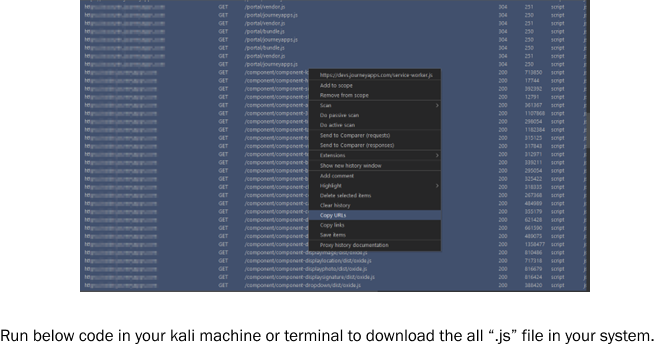
- Extracting JavaScript file with burp suite: Make sure you set up your burp proxy and keep it running in background. Take a deep dive into your target, thoroughly examining all its features and endpoints. Once you’re done, head over to the proxy tab and configure the filters as shown below to capture all the JavaScript files. Don’t forget to copy all the results and save them in a file called “link.txt”.
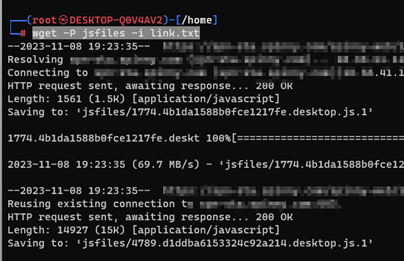
· wget command, which can retrieve files from the web using HTTP and FTP protocols. · -P option can be used to specify a different directory to save the files. · -i option specifies a file that contains a list of URLs to download.
After this step, you can visit each file and check for some of keywords manually such as “api key, api_key, password, secret, token, access, pwd, url, config, aws, s3” etc.
Feel free to check out the GitHub repository below for additional examples of regular expressions:
https://github.com/l4yton/RegHex?source=post_page—–c95a8aa7037a——————————–
If you find any sensitive token or key then you can use this below repository to take your exploitation part further.
https://github.com/streaak/keyhacks
Automated extraction of JavaScript code:
Following are the required Tools for this process. Install these tools in your kali or system from these repo and installation links below:
· Gau: https://github.com/lc/gau
· Waybackurls: https://github.com/tomnomnom/waybackurls
· Httpx: https://github.com/projectdiscovery/httpx
· Subjs: https://github.com/lc/subjs
· Nuclei: https://github.com/projectdiscovery/nuclei
Save this below code in bash file at your system. Here “target.txt” contains your target domains.
Here is the explanation of each command:
1. cat target.txt | gau | grep “.js” | tee js.txt
cat target.txt | waybackurls | grep “.js” | tee -a js.txt:
This command reads the contents of the target.txt file, pipes it to the gau and waybackurls tool to extract URLs, pipes the output to grep to filter out only the URLs that contain .js, and finally pipes the output to tee to write the results to the js.txt file.
2. cat target.txt | subjs | httpx -mc 200 | tee -a js.txt:
This command reads the contents of the target.txt file, pipes it to the subjs tool to extract JavaScript files, pipes the output to httpx to check the status code of each file, filters out only the files with a status code of 200, and finally pipes the output to tee to append the results to the js.txt file.
3. nuclei -l js.txt -t /root/nuclei-templates/http/exposures/ -o js_bugs.txt:
This command uses the nuclei tool to scan the JavaScript files stored in the js.txt file for vulnerabilities using the templates located in the
/root/nuclei-templates/http/exposures/ directory.
The results of the scan are stored in a file named js_bugs.txt.
Though these above steps we have now got the “js.txt” file which contain all JavaScript file.
Hunting for secrets in JavaScript:
Hunting for secrets through Mantra “Mantra” is a tool used to hunt down API key leaks in JS files and pages, you will find the GitHub repository and installation steps for this tool in below link.
Mantra: https://github.com/MrEmpy/mantra
Command: cat js.txt | Mantra
Hunting for secrets through Secret Finder:
Secret Finder: https://github.com/m4ll0k/SecretFinder
1. cat js.txt: This command reads the contents of the js.txt file which contains all js files of our target.
2. while read url;do python3 SecretFinder.py -i $url -o cli ; done:
This command uses a while loop to read each URL from the js.txt file and pipes it to the Secret Finder tool. The -i flag specifies the input file, and the -o cli flag specifies that the output should be written to the command line. The results of each scan are displayed in the command line.
3. endpoints: This command writes the output of the entire command to the endpoints file.
You can find the results similar to the below screenshot.
In addition to the above tools, JS Miner is another tool that can be used to scan JavaScript files for secrets, URLs, and other sensitive information. This tool comes as a Burp Suite extension and hence it is very handy. GetJS is also a tool that can be used to extract .js files from a list of domains. Once the .js files are extracted, they can be searched for specific keywords to identify potential vulnerabilities.
JavaScript files are considered as treasure in modern day web applications. Sometimes, developers might mistakenly leave some sensitive information such as API keys, data base connection details on client-side script. Thus, it is imperative to look for secrets and sensitive information inside JavaScript files. We hope that this article has provided you with valuable insights on how to optimize your time and effectively discover secrets in the JavaScript code.
